Given the constantly changing digital business operations, Third-Party Risk Management (TPRM) is crucial to strengthen your cybersecurity posture. You may face challenges with complex relationships with suppliers, manufacturers, service providers, and business partners that expose you to financial, environmental, reputational, and security risks.
Additionally, managing your suppliers can take excessive time to complete this process manually, especially if new suppliers are frequently being added to your supply chain. This article addresses key questions related to third-party risk management that can help you manage such risks effectively.
Understanding the Third-Party Landscape
Defining Third and Fourth Parties
A third party is broadly any external entity collaborating with your business; this can span your network of suppliers, manufacturers, service providers, and more. Delving deeper, fourth parties or “Nth parties” are entities connected through your third parties, adding additional layers to your supply chain.
What is the Importance of Third-Party Risk Management?
The significance of TPRM lies in its profound impact on your organisation’s cybersecurity posture. Third parties add another layer of complexity to your business due to the lack of control and transparency in their security measures. Each entity presents a potential entry point for cyber threats, increasing the attack surface and potential for vulnerabilities.
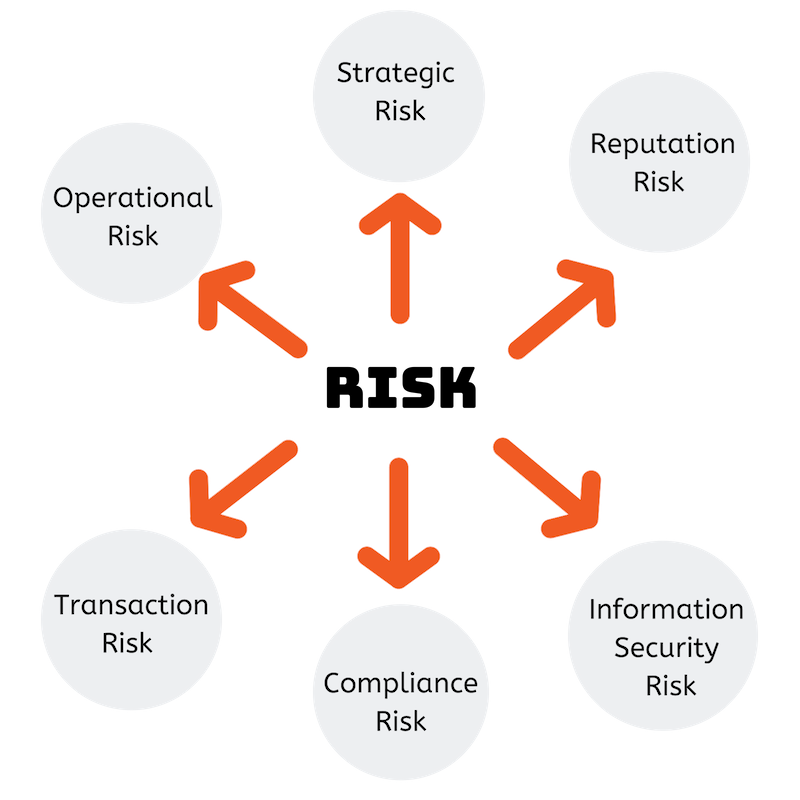
Unveiling the Risks Introduced by Third Parties
Cybersecurity Risk
Your exposure to cyber threats, breaches, and security incidents requires rigorous due diligence and continuous monitoring of vendors.
Operational Risk
Potential disruptions to your business operations demand contractual service level agreements (SLAs) and comprehensive incident response plans.
Legal, Regulatory, and Compliance Risk
The risk of third parties affecting compliance with local legislation, regulations, and agreements is particularly critical in sectors like finance, healthcare, and government.
Reputational Risk
Negative public opinion stemming from third-party actions, especially data breaches, can substantially threaten your organisation’s reputation.
Financial and Strategic Risks
Third parties can significantly influence your organisation’s success, from financial impacts to hindering strategic objectives.
Investing Wisely: Reasons to Engage in Third-Party Risk Management
Cost Reduction
You can reap substantial long-term cost savings when you view TPRM as an investment. You can significantly reduce the likelihood and cost of data breaches by effectively managing third-party risks.
Regulatory Compliance
To stay aligned with cybersecurity frameworks and regulatory requirements like DORA, NIS2, Cyber Essentials, and NIST, it’s vital to consider TPRM as a cornerstone for legal adherence and industry standards.
Risk Reduction
Streamlining vendor onboarding and continuous monitoring mitigate the risks of security breaches and data leaks.
Knowledge and Confidence
Enhanced visibility into third-party vendors fosters informed decision-making across all stages of the partnership.
The Role of Vendor Management Policy
Identifying High-Risk Vendors
A well-crafted vendor management policy identifies high-risk vendors. It defines controls to minimise third-party and fourth-party risks.
Evaluating Vendor Relationships
Assessment of vendor contracts, annual inspections, and adherence to security standards ensures a robust vendor management framework.
Evaluating Third Parties: Methods and Solutions
Security Ratings
Our TPRM service uses security ratings to provide real-time insights into third-party risks, aiding in cyber insurance underwriting and government compliance.
Security Questionnaires
Efficiently identify potential weaknesses through third-party risk assessments using security questionnaires streamlined by our service.
Virtual and Onsite Evaluations
External reviews, including policy and procedure assessments, comprehensively understand a vendor’s security controls.
Overcoming Common Challenges in TPRM
Speed and Efficiency
Our TPRM service prioritises speed, streamlining the vendor assessment process for faster and more efficient risk evaluations.
Depth and Visibility
Automated tools such as our TPRM service ensure monitoring of all vendors, regardless of perceived risk, providing comprehensive visibility.
Consistency and Standardisation
Standardised checks across all vendors while assessing critical vendors more rigorously ensure a consistent and reliable evaluation process.
Context and Trackability
Labelling vendors based on criticality provides context, aiding security teams in prioritising and effectively utilising time and budget resources.
Engaging Stakeholders
Effectively communicating cybersecurity importance to vendors involves overcoming challenges and aligning perspectives.
In conclusion, embracing a holistic approach to Third-Party Risk Management is imperative in safeguarding organisations from multifaceted threats. Through a meticulous process encompassing analysis, engagement, remediation, approval, and monitoring, coupled with robust policies and evaluation methods, organisations can fortify their cybersecurity posture and confidently navigate the complex landscape of third-party relationships.
My Name is Sandra Butler and I am also the main source from the ‘Seeheadlines.com’ of all the exclusive and most delicate visualization of the activities in the business sector. My first step towards this journey was taken in the very early years of my life. I started with an independent financial consultant. However, I only had almost 4 years of skills and experience in this market.